Monitoring approach
Monitoring infected IoT devices has three main objectives:
- providing new means to understand the existing and emerging threats that are targeting the Internet of Things;
- characterizing infected IoT devices by performing active measurement;
- generating a daily data feed on infected devices including their characteristics such as firmware version and manufacturer.
At the core of the monitor, a hybrid honeypot lies to identify infected IoT devices and characterize them. This type of monitoring fulfills a set of desirable properties:
- Low number of false positives;
- Real-time alerting of highly-probable threats as soon as they occur, enabling rapid response before an attack has the opportunity to spread.Honeypots are capable of alerting first-responders to highly-probable threats as soon as they occur, enabling rapid response before an attack has the opportunity to spread
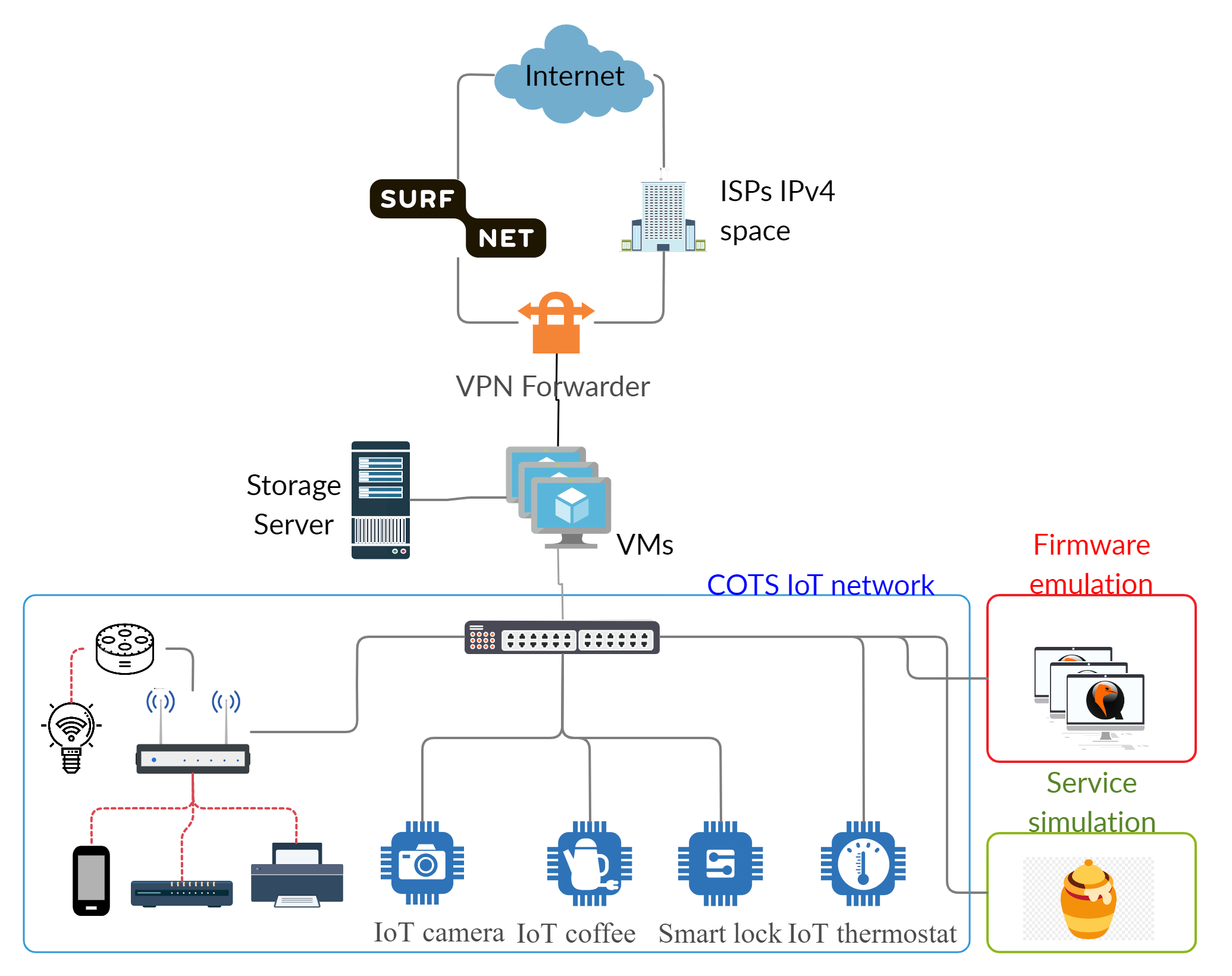
This monitor is located in the basement of the Technology, Policy and Management faculty consists of different hardware and software components.
Physical honeypot
To capture attacks targeting particular vulnerabilities of IoT devices present in the Dutch consumer market, the monitor is equipped with a subset of Commercial Off-The-Shelf (COTS) devices proven to be vulnerable and exploited by IoT botnets.
These devices are selected not only because of their market penetration, but also based on their availability, lack of automated patches, ability to downgrade the firmware, and their use of default credentials. On the contrary, infection vectors leveraging dictionary attacks are captured by the software-based honeypot. Up to now, we have acquired a set of devices that actually fulfill the aforementioned requirements.
Software-based honeypots
Beyond the actual physical devices, our honeypot also implements a set of vulnerable services that are emulated in multiple virtualized machines. The infrastructure is shown in the figure below.